2021-2-20 22:53 |
The DeFi community is once again questioning the “test in prod” approach after an exploit left Alpha Finance Labs and CREAM Finance $37.5 million short. This week, BeInCrypto looks at five DeFi projects that successfully came back after being exploited.
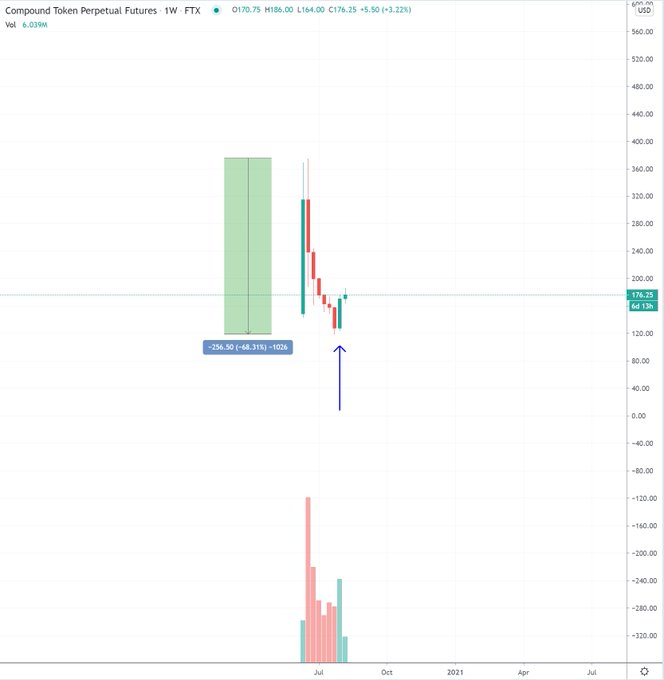
1. Compound (COMP)COMP is a decentralized finance (DeFi) lending platform that allows users to borrow and stake to lend without the need for third parties.
It currently has over $5.25 billion in total value locked (TVL). This makes it the third largest DeFi project, behind Aave (AAVE) and Maker (MKR).
In November last year, an error or malicious attack exploited a Coinbase oracle which the platform used to set the value of the dai (DAI) stablecoin. The bug or attack caused the price of the stablecoin to reach $1.30.
As Compound loans require over-collateralization, the sudden surge in dai price left borrowers under collateralized, and therefore many were liquidated.
2. Yearn Finance (YFI)On Feb 5., 2021, Yearn Finance’s yDAI vault saw an exploit that resulted in the loss of $11 million.
The exploit involved a series of flash loans taken out from dYdX and Aave pools. The hacker responsible then used these loans as collateral for another loan on Compound’s platform.
Essentially, the hacker attempted to benefit from the price difference in Yearn’s vaults to accumulate Curve DAO Token (CRV) to sell for stablecoins.
In what may have been a silver lining, the hacker reportedly didn’t pocket the full $11 million as fees for the attack totaled $8.5 million.
We have noticed the v1 yDAI vault has suffered an exploit. The exploit has been mitigated. Full report to follow.
— yearn.finance (@iearnfinance) February 4, 2021 3. SushiSwap (SUSHI)SushiSwap is an automated market maker (AMM) that forked from rival Uniswap last year amidst a row over centralization.
In January this year, an opportunistic SUSHI user discovered a loophole that allowed them to effectively steal 81 ETH (worth around $103,842, at the time).
The exploit involved a transaction using Badger DAO’s DICG token. The transaction attempted to convert a small amount of the fees in a DICG/WBTC pool through a DICG/ETH pool.
The latter had extremely low liquidity (and therefore high slippage) resulting in relativity high fees. The opportunistic hacker essentially attempted to claim those fees, making use of a bug that redirected fees from stakers.
It must be noted however, that the amounts involved were relatively small with one Twitter user claiming the exploit was limited in impact.
Old loopholes opened up give a hacker a small reward.
24 hours of DIGG/WBTC swap fees snatched by an opportunist.
It ain't much, but is it honest work?
We spoke to the @SushiSwap team to find out what went wrong.https://t.co/mSTTXTtarg
The Cover Protocol exploit is probably the most dramatic on this list. This time, a white-hat hacker from Grap Finance (although this wasn’t known, at the time), used an exploit to mint 40 quintillion COVER tokens.
These tokens were in direct control of the hacker who promptly withdrew the tokens to Binance. The surge in supply, as well as the hacker’s “dumping” in COVER/ETH markets, caused the price of COVER to fall over 50% in minutes.
Moreover, as the market coined on to what was taking place, the token’s value dropped to below $100 from a height of $720. The attack prompted Binance to suspend trading, as well as the Cover Protocol team to suspend the token all-together.
Luckily, the hacker returned the funds and Binance even reimbursed traders who had “bought the dip” from its own SaFu fund.
Next time, take care of your own shit.@CoverProtocol @chefcoverage https://t.co/ks94ucdoRQ
1. No gains.
2. The Obtained Funds from LP has been returned to COVER.
Finally, the most recent exploit involved Alpha Finance Lab’s newly released Homora v2 and CREAM Finance’s Iron Bank.
The exploit resulted in a hacker managing to extract $37.5 million. According to a post mortem of the exploit, the exploit involved loans from Homora v2 being deposited in CREAM finance’s Iron Bank.
ALPHA users familiar with the exploit pointed out that only someone with knowledge beyond what was accessible publicly could have been responsible for the attack.
Indeed, the post mortem confirmed this. It stated that the particular funding pool used in the exploit sat at the contract level on HomoraBankV2 in preparation for an upcoming launch.
The post 5 DeFi Projects That Successfully Came Back From Exploits/Hacks appeared first on BeInCrypto.
origin »Bitcoin price in Telegram @btc_price_every_hour
Compound Coin (COMP) на Currencies.ru
|
|