2020-6-9 23:01 |
The digital forensics firm Crypsis Group recently released a report on ransomware attacks and how the demand for ransom amounts has grown significantly by 200% from 2018 to 2019.
The report also detailed that, over the years, the amount of demanded Ransom by the attackers has grown dramatically. The average amount of ransom asked by these attackers has reached $115,123.
The report further revealed that these ransomware attackers have now shifted their focus towards enterprises and big players who they know can pay a higher ransom, rather than smaller individuals. The methods of attacks, attack tactics, and victim manipulation have also matured over the years.
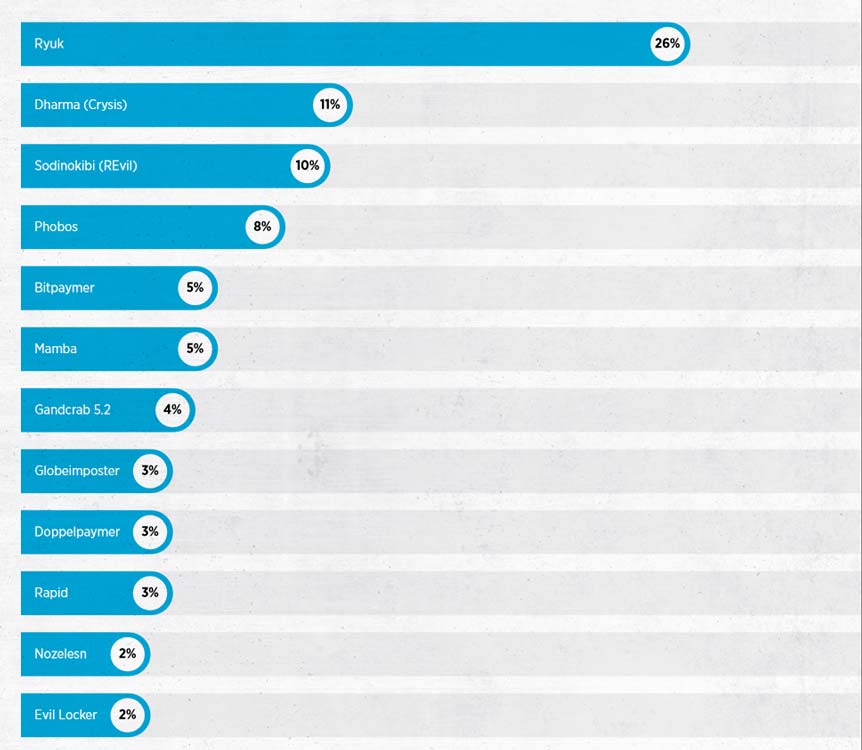
Popular Choice of Malware For Ransomware AttacksCrypsis Group report also listed some of the popular malware used for ransomware attacks in recent times which included Ryuk, Sodinokibi (or “REvil”), and Phobos. Among the mentioned three ransomware variants, Ryuk has been the favorite of scammers and was also the most used variant in 2018.
Most Common Ransomware VariantsThese attackers make use of TrickBot, which is a banking Trojan in the form of phishing emails or even pop-ups. When the victim clicks on the link, the malware is quietly transferred into the system which is very difficult to detect. The malware then ends up gaining control over the system and attackers demand a ransom amount, usually in cryptocurrency, to give access back to the company.
Another report from Verizon last month revealed that in 2020, a majority of these ransomware attackers targetted educational institutions.
Ransomware attacks have been one of the worst nightmares for private sector enterprises including crypto exchanges like Binance as well as government agencies who have fallen prey to these kinds of attacks. While the government has tried to educate the masses about these attacks, they have largely failed to contain the issue.
These ransomware attackers adapt quite fast to the changing security services and despite their malware getting banned a number of times, they come back with a different malware name and more elaborate sophisticated tools to avoid being detected.
origin »Bitcoin price in Telegram @btc_price_every_hour
Digital Rupees (DRS) на Currencies.ru
|
|





