Vectors - Свежие новости [ Фото в новостях ] | |
Protect Your XRP: 6 New Phishing Tactics Identified by XRPL Contributor Wietse Wind
Wietse Wind issues an urgent security briefing on a massive XRPL scam campaign in February 2026. Learn the six specific phishing vectors targeting XRP holders and how to secure your coins today. дальше »
2026-2-17 18:57 | |
|
|
Ethereum Foundation backs SEAL to combat rising threat of crypto drainers
Crypto security nonprofit Security Alliance has received a sponsorship from the Ethereum Foundation as it ramps up efforts to curb crypto drainers and other attack vectors targeting Ethereum users. According to SEAL, the Ethereum Foundation has sponsored a security engineer… дальше »
2026-2-10 11:04 | |
|
|
Depeg crisis of real estate-backed USDR stablecoin deemed terminal as protecting users ‘impossible’
TangibleDAO will discontinue its real estate-backed USDR stablecoin stablecoin project after it depegged on Oct. 11. In an Oct. 12 post on X (formerly Twitter), the project said the stablecoin has too many attack vectors in its design, and measures designed to protect its users were easily manipulated. дальше »
2023-10-12 15:30 | |
|
|
Adobe Firefly 2 brings vectors to generative AI tools in Creative Cloud suite
At their annual Adobe MAX conference, Adobe unveiled new generative AI models that aim to enhance creative workflows. The models include Firefly Image 2, Firefly Vector, and Firefly Design. Firefly Image 2 builds on the previous version’s image generation capabilities. дальше »
2023-10-11 15:35 | |
|
|
Another week, another sorry tale of blockchain hacks
In terms of scale, the $200 million Mixin Network cloud service provider database hack stood out. Security vulnerabilities and phishing incidents were the most utilized attack vectors. WhileThe post Another week, another sorry tale of blockchain hacks appeared first on AMBCrypto. дальше »
2023-10-2 16:30 | |
|
|
Movement Labs raises $3.4M to further develop smart contract language Move
Movement Labs said it raised $3. 4 million in pre-seed funding to boost the security and adoption of its Web3-based Smart Contract Language, Move. According to a Sept. 13 statement shared with CryptoSlate, Move is a programming language with embedded safeguards that protects projects from common attack vectors like reentrancy that have cost the industry billions […] The post Movement Labs raises $3. дальше »
2023-9-13 19:15 | |
|
|
PayPal’s stablecoin has wallet freezing and wiping functions
An analysis of the smart contract of the just-launched PayPal stablecoin PYUSD revealed the presence of so-called “centralization attack vectors.” Smart contract security auditor Pashov pointed out in a recent Twitter thread that PYUSD’s contract has an ‘assetProtection’ role. It… дальше »
2023-8-8 17:49 | |
|
|
Compound DeFi platform announces Borrow caps for V2 assets.
Compound, in a recent statement, announced that at the end of November, the firm will implement loan limitations on 10 version 2 protocol crypto tokens. The implementation is aimed to reduce high- risk attack vectors. дальше »
2022-11-29 19:26 | |
|
|
Harpie Review: Can This On-Chain Firewall Solve Web3’s Security Problem?
Harpies on-chain firewall lets crypto users connect their Web3 wallets and create a safe transacting environment and protect themselves against cryptos most common attack vectors. Cryptos Security Problem As crypto... дальше »
2022-11-1 17:17 | |
|
|
How North Korea Infiltrated The Crypto Industry Using Fake LinkedIn Resumes
Per a Bloomberg report, North Korean-backed hackers might be stepping up their efforts and attack vectors against the crypto industry. Bad actors seem to be stealing resumes and information from major job listings websites to apply for jobs in the nascent sector. дальше »
2022-8-2 23:48 | |
|
|
Kraken finds 'multiple attack vectors' in top Bitcoin ATM producer's range
Vulnerabilities found in DeFi protocols and other crypto-platforms are a recurring phenomenon within the industry. However, Kraken Security Labs has found that a "large number" of Bitcoin ATMs are vulThe post Kraken finds 'multiple attack vectors' in top Bitcoin ATM producer's range appeared first on AMBCrypto. дальше »
2021-10-1 22:00 | |
|
|
Flash Loans and Duplicate Websites Continued to Plague Crypto Platforms in July
Over July, there was a flurry of sophisticated cyberattacks within the crypto. Cybercriminals continue to exploit a variety of attack vectors in the pursuit of siphoning off digital currencies. The post Flash Loans and Duplicate Websites Continued to Plague Crypto Platforms in July appeared first on BeInCrypto. дальше »
2021-8-3 19:00 | |
|
|
Top 5 home cybersecurity systems to protect your data and digital assets
As new smart devices provide a myriad of new attack vectors for bad actors to infiltrate your home, use these 5 systems to shield your private data and digital assets from unwanted attention. The post Top 5 home cybersecurity systems to protect your data and digital assets appeared first on CryptoSlate. дальше »
2021-6-3 15:23 | |
|
|
The U.S. just got a ‘pure-play’ Bitcoin and crypto ecosystem ETF
Global investment manager VanEck launched its ‘Vectors Digital Transformation ETF’ (DAPP), yesterday, as per a release. The post The U.S. just got a ‘pure-play’ Bitcoin and crypto ecosystem ETF appeared first on CryptoSlate. дальше »
2021-4-15 16:00 | |
|
|
A Fraud Risk Management Framework For The Bitcoin Ecosystem
As fraudsters exploit attack vectors that enable bitcoin double spends, merchants should be aware of options to mitigate their risk. The post A Fraud Risk Management Framework For The Bitcoin Ecosystem appeared first on Bitcoin Magazine. дальше »
2020-12-15 17:32 | |
|
|
Lightning Network Exploits Continue to Hinder the Bitcoin Scaling Solution
While bitcoin has run-up to all new price highs in 2020, a great number of crypto supporters have been complaining about the mempool backlog and the high fees needed to send a transaction. Meanwhile, the Lightning Network is far from seeing widespread adoption, and a number of attack vectors have been revealed this year. дальше »
2020-11-1 07:45 | |
|
|
Here’s How Hackers Stole $22M From Electrum Bitcoin Wallet Users
Hackers continue to use a simple malware exploit to steal Bitcoin (BTC) from unsuspecting Electrum wallet users. From malware attacks to cryptojacking exploits and attack vectors, malicious entities continue to devise means to steal cryptos. дальше »
2020-10-13 23:30 | |
|
|
Malevolent insiders and software errors: researchers revealed main hacking attack vectors on exchanges
At the Black Hat Security Conference, researchers detailed potential attack points that could be exploited by attackers to steal cryptocurrencies. Among the examples given were real cases that affected the operation of existing cryptocurrency exchanges. дальше »
2020-8-15 00:46 | |
|
|
Never Underestimate a Cryptocurrency Dusting Attack
In the cryptocurrency world, there are numerous attack vectors. Users need to be aware of all potential problems at every waking moment. Dusting attacks are seemingly becoming slightly more common over the years. дальше »
2019-8-18 04:00 | |
|
|
UN: North Korea Cyberattack Methods Revealed
Following revelations that North Korea amassed $2 billion in cryptocurrency for weapons programs, a new report discloses further details. According to the United Nations, it is investigating a total of 35 North Korean cyberattacks in 17 countries. дальше »
2019-8-13 16:00 | |
|
|
This cryptocurrency stealing malware was blocked more than 360,000 times over the past year
As long as cryptocurrency has value, people will try to steal it. According to the latest figures from cybersecurity firm Avast, a cryptocurrency stealing malware has been blocked more than 360,000 times by its software. дальше »
2019-8-6 14:47 | |
|
|
Monero security flaw could’ve seen XMR stolen from cryptocurrency exchanges
Privacy-focused altcoin Monero has suddenly disclosed nine security vulnerabilities — including one that could have allowed hackers to steal XMR from cryptocurrency exchanges. Until March, rogue Monero miners were hypothetically able to create “specifically-crafted” blocks to force Monero wallets into accepting fake deposits for an XMR amount chosen by the attacker. дальше »
2019-7-4 18:18 | |
|
|
No, Courts Cannot Force Changes, Ethereum (ETH) Bullish Above $170
Ethereum prices up but bears may stage a comeback Decentralization effectively neutralizes threats Jimmy Song, a Bitcoin supporter, asked a question on matters touching decentralization and Vitalik answered him correctly. дальше »
2019-4-12 21:00 | |
|
|
Trezor Defends Crypto Wallet Security after Ledger’s MIT Bitcoin Bombshell
Ledger Chief Security Officer Charles Guillemet gave a shocking presentation at the MIT Bitcoin Expo this week in which he presented alleged vulnerabilities with the hardware cryptocurrency wallet produced by Trezor – perhaps its top competitor. дальше »
2019-3-13 23:07 | |
|
|
Validators Create New Attack Vectors for Decentralized Systems
Bounty0x CMO Pascal Thellman discusses some of the potential security and incentives issues with validators on proof-of-stake networks. дальше »
2019-2-24 14:30 | |
|
|
BetterHash Protocol Lets Pool Miners Regain Control Over Their Hash Power
One problem that concerns many is the centralization of mining within the Bitcoin ecosystem. Fortunately, there are talented developers working to solve this problem and Matt Corallo, full-time Bitcoin developer at Chaincode Labs, is one of them. дальше »
2019-1-26 23:50 | |
|
|
Neutrino: A Privacy-Preserving Light Wallet Protocol
Lightning is all the rage these days and, while it's an exciting development, users currently have to have a full node running in order to transact in it. In this article, I'm going to introduce Neutrino, a new protocol for light clients to get the data that they need while preserving privacy and without trusting a central server. дальше »
2019-1-4 21:11 | |
|
|
Hardware Hacking: How To Secure Your Trezor Wallet With Passphrase
A group called wallet. fail gave a presentation on how to hack cryptocurrency hardware wallets at the 35th Chaos Communication Congress. While all attack vectors required physical access, worryingly, the group demonstrated scraping the seed and PIN from Trezor RAM. дальше »
2018-12-29 02:00 | |
|
|
McAfee Labs Report: Crypto-Jacking Malware Mining Several Coins on Host System Detected
A report submitted by McAfee researchers on November 12, 2018, claims that a new crypto mining malware capable of mining different cryptocurrencies depending on the host’s system is on the loose. Russian Malware Attacks Global Networks Crypto-jacking malware and its attack vectors are becoming more efficient by the day. дальше »
2018-11-16 20:00 | |
|
|
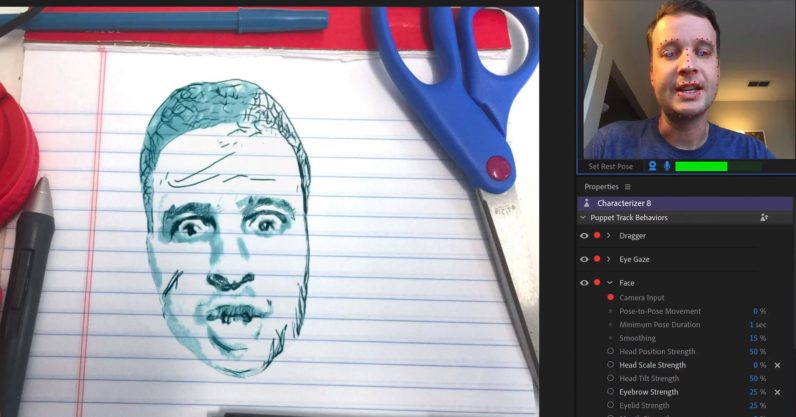
Adobe Characterizer turns you into an animated drawing with the power of AI
When I was a kid, I briefly held the aspiration of making my own cartoons. I dabbled in the animation portion of Flash and made a few cheesy . flvs, but soon realized I wasn’t up to the task of dealing with keyframes and drawing pretty vectors. дальше »
2018-10-17 20:28 | |
|
|
Bitcoin Price Analysis: Centralization of Mining Pools open Up New Attack Vectors
After losing four percent in the last week mostly compounded by strong losses of Oct 11, sellers are in control. This view is regardless of our expectations of higher highs in the aftermath of deflating dips of last week. дальше »
2018-10-15 05:00 | |
|
|
Deloitte: Five Areas Can Help Overcome Barriers to Blockchain Adoption
A report authored by three Deloitte analysts explains the barriers to blockchain adoption and how the “five vectors of progress” may help companies lower the cost and risk of deploying and exploring the technology. дальше »
2018-10-2 00:00 | |
|
|
North Korean hackers are targeting cryptocurrency traders with fake software
North Korean hacking outfit “Lazarus” is now targeting cryptocurrency exchanges. Information security firm Kaspersky Labs has discovered it is exploring new attack vectors and trojanizing cryptocurrency software. дальше »
2018-8-23 16:05 | |
|
|
How Peter Kroll’s Paper Wallet Protects Cryptocurrency
Since its invention, a recurring question for cryptocurrency holders has been how to best secure their digital assets. This question of security carries the greatest weight when one understands the stakes of holding unprotected cryptocurrency — vulnerability to hackers. дальше »
2018-7-6 03:51 | |
|
|
Warning! Trezor wallet undergoes phishing attack, team offers security advice
Trezor wallet recently underwent a phishing attack, according to Trezor’s official blog post. They mentioned that they were facing complaints of an invalid Secure Sockets Layer [SSL] certificate. The certificate warning was said to have raised with respect to phishing attempts on the site. дальше »
2018-7-3 23:19 | |
|
|