2018-12-1 10:29 |
From the CMC editorial desk: We asked this all-important question to Sentinel Protocol, a company setting out to solve just this problem. With their expertise in security, what does their solution look like? Here we go!
While the pace of ICO fundraising may have slowed down recently, ICOs are still a hot topic in the realm of cryptocurrency investments. The size of the average funding round and the rate of project funding are higher than ever in 2018.
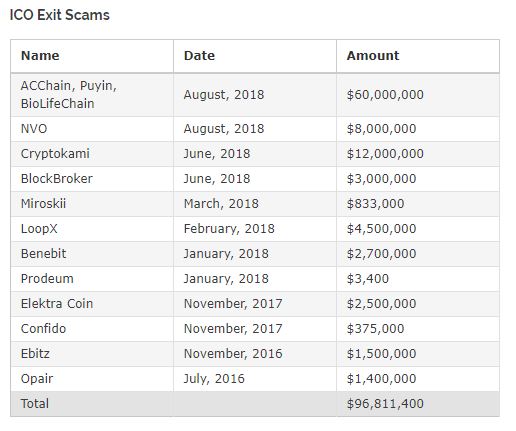
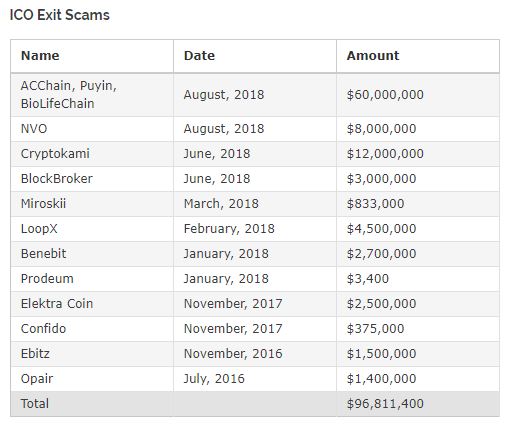
ICOs are often synonymous to risk and hype. When they take place, the project is usually only at an early stage, trying to justify the greatness of its team and advisors, tokenomics, or even the need to use blockchain technology in the first place. From an investment perspective, it may be difficult to identify great projects from the good, and good ones from the bad. The bad ones might be called “scams” by those who were burnt by subpar returns. The scams we’re discussing in this post, however, is of a different type – it is about checking the validity of information exchanged between an investor and the ICO project.
Two main reasons why individuals are easy scam targetsIn the centralized world, there are institutions to provide security against fraud and they can also report fraudulent activity to the police. In the decentralized world, this responsibility is imposed onto individuals, forcing them to protect themselves from scams and hacks. In the real world, you can call the credit card company to block your card if it gets stolen. But in the crypto world, your stolen crypto is out in the open.
The problem is that crypto individuals are not accustomed to checking whether transaction data is authentic or malicious. Secure online behavior needs to be acquired over time, as it is a behavior that is learnt through specific education or repetitive practices. The practices of checking if the website is not a phishing site, or if the wallet address is not compromised, are often overlooked by those who have never been victimized before.
Another problem is that crypto individuals are not capable of doing a proper security check, simply because they are not experienced in it. If it is a really well-crafted scam, carefully designed by malicious actors, crypto individuals by far lack the capability to detect such scams on their own. For example, tips have been shared among the community to check the SSL certificate on each website. But if the tips involve checking any code or detecting spoofed emails, not everyone has the capability or awareness to do such deeper security checks on their own.
ICO projects are no exceptions to falling for scamsAlthough not widely publicized, ICO projects are also major targets for scammers. When we held our own ICO for Sentinel Protocol, we witnessed many scam attempts towards us too. It’s not just careless ICO participants contributing to the wrong wallet address, visiting a phishing site, or falling for the Twitter giveaway scams.
Example: Solicitous offer email impersonating a well-known ICO review site
Personal messages from advisors on Telegram, and emails from ICO review and listing sites are part of the ICO lifecycle. Due to this, Telegram handles and email from similar domains could be easy to impersonate. Some syndicates try to sabotage sales or forge KYC submissions. Being a security company ourselves, with in-house security experts who do digital forensics and threat research full-time, we managed to block these attempts successfully. But imagine how an ICO project without the same experience in security would fare, being without the resources to hire full-time experts who can distinguish malicious data from seemingly legitimate information.
On top of ICO projects already receiving constant queries from investors about scams by impersonators pretending to be the official ICO project, the team members themselves need to be extra careful about scam attempts targeting the team. Indeed, quite often, conventional security breaches usually occur on the inside. Crypto companies, the ICO projects, are also not immune to this.
A simple solution with a difficult implementationDue to the nature of these threats, a solution would require an approach that incorporates contributions from different parties with their own unique skills and perspectives. This multifaceted solution, however, should not confuse individual users by its high-level sophistication.
This makes it a multi-faceted problem, mainly: (1) It has to be a feasible and direct solution to the scam problems most often detected; (2) It requires actual knowledge of these problems and how to solve them; (3) The user experience must be seamless and easy to adopt even by those new to ICOs.
Making a comprehensive threat database accessibleSince scam and fraudulent attempts are ever-growing and malicious data appears in bits and pieces everywhere around the world, it would not be a complete arsenal of comprehensive threat data if we did not use collective intelligence. As a team of cybersecurity experts with industry knowledge, we understood that using this collective intelligence to build a decentralized threat database is otherwise not possible without blockchain technology.
These considerations formed the backbone of this Threat Reputation Database (TRDB), developed to collect as much data on scams and fraudulent activities as possible. The system relies on a network of security experts called “The Sentinels” who are globally distributed and incentivized to leverage their security expertise within the token economy.
Illustration: How TRDB and The Sentinels gather, verify, and share Data
Of course, we still need the expertise and pre-existing knowledge to kickstart the process of populating the database. By roping in the “Pre-Sentinels”, who have been interviewed and whose security expertise has been verified, we bootstrap the first repository of threats upon which others in the token economy can build. Collectively, they are building a whitelist for authentic ICO data and a blacklist for malicious ICO data to display what legitimate information ICO participants can safely access.
As we also mentioned, to ensure individuals are able to distinguish scams without high overhead, an easy-to-use solution is paramount for it to become the gold standard in dealing with crypto scams out there today. For this reason, a Chrome Extension was chosen as the first iteration of the product. By tapping into this extension, the chances of sending a contribution to the wrong address is reduced, simply by double-checking whether the site being visited is authentic or whether the wallet address is the correct one.
Reducing security threats around the worldFor most, it already takes a lot of research to find great ICO projects to invest in, so it is important to ensure that the resources put into it are legitimately used with little risk of being scammed in the process. A security solution like the TRDB ensures that the know-how of the crowd is being applied to aid the larger public in accessing authentic data and platforms.
As our blockchain applications become more advanced, the threats will also become more sophisticated. We believe that solutions should be more user friendly so that more people can benefit from them. Cybersecurity is becoming increasingly prevalent in today’s world as cyber-terrorism grows. To combat cyber attacks, we have to work together to ensure that we protect each other from these malicious actors.
Sentinel Protocol is the first crowdsourced threat intelligence platform built on the blockchain. It collects and analyzes information about real-time hacks, scams and fraud to improve security of crypto assets and shares this intelligence with crypto exchanges, wallets and payment services using a decentralized Threat Reputation Database (TRDB).
The post How to Combat Scams in ICO Investing appeared first on CoinMarketCap.
Similar to Notcoin - Blum - Airdrops In 2024
ICO OpenLedger (ICOO) на Currencies.ru
|
|